Zero Trust is all the rage lately, and traditional VPNs are getting a lot of scrutiny since they essentially add and remove encryption at the firewall. This means bad actors can skip off into the sunset (laterally) and gain access to those legacy systems with less effort. Another challenge with using a traditional VPN is scaling with the dramatic shift to hybrid work. ZeroTier is an interesting solution that claims to combine the capabilities of VPN and SD-WAN, among other things. Let’s take it for a spin.
Most tech these days supports HTTPS. How hard could Zero Trust be? Anyone that has managed certificates in a large enterprise can answer this question. It is more complicated than it may appear to be on the surface. And as you begin removing that complication, you start trusting identity providers and certificate authorities more broadly. One question that must be asked is, if you are using any number of Zero Trust solutions hitting the market, are they Zero Trust when you trust them to own everything?

Scenario#
I know many people (myself included) that want to access devices on their home network while they are away. A solid example here is security cameras or maybe a lab environment that you can test with while traveling. I wouldn’t want to make my home cameras reachable directly from the internet.
One way you could solve this problem is by hosting an OpenVPN server on your network, so when you are away, you can fire up the mobile app, connect, and check out what is going on around your property. How would these scenarios work with ZeroTier? Let’s lab it up!
First, What is ZeroTier?#
ZeroTier is a Mesh VPN solution. Mesh VPNs facilitate connectivity directly between any two endpoints in the mesh without having to transit through a concentrator in a data center. Sessions between every pair of endpoints are encrypted end-to-end. If a bad actor can exploit a device, they only gain visibility into the traffic coming in and leaving that device, making lateral movement a challenge.
ZeroTier Network Hypervisor#
ZeroTier’s network hypervisor is a custom protocol that implements a VXLAN like ethernet virtualization across two layers:
- Virtual Layer 1 (VL1): is the underlying peer-to-peer transport layer handling encryption, endpoint authentication, and credential verification
- Virtual Layer 2 (VL2): overlays boundaries, multicast, rule enforcement, and certificate-based access control on (VL1)
Want to dig deeper into ZeroTier’s Network Hypervisor? Check out the Protocol Design Whitepaper for a transparent explanation of ZeroTier’s services, apps, and libraries. Remember, sufficiently advanced technology is like magic until you read the docs!
What is OPNsense?#

OPNsense is an open-source security platform based on FreeBSD. I have used it historically as an entry point into various lab environments and as a customer-side appliance to terminate site-to-site VPNs for various public cloud providers. Since the platform offers LDAP and 2FA, extending access to others for collaboration is simple. OPNsense offers a ZeroTier Plugin and supports dynamic routing via FRR.
You may be asking, why are we installing this on a firewall given the peer-to-peer architecture of ZeroTier? By installing ZeroTier on the firewall, it acts as a bridge of sorts between all the devices on my test network and the outside ZeroTier members I authorize. In doing this, I don’t have to install the ZeroTier client on each device I want to talk to when operating remotely.
Setting up ZeroTier#
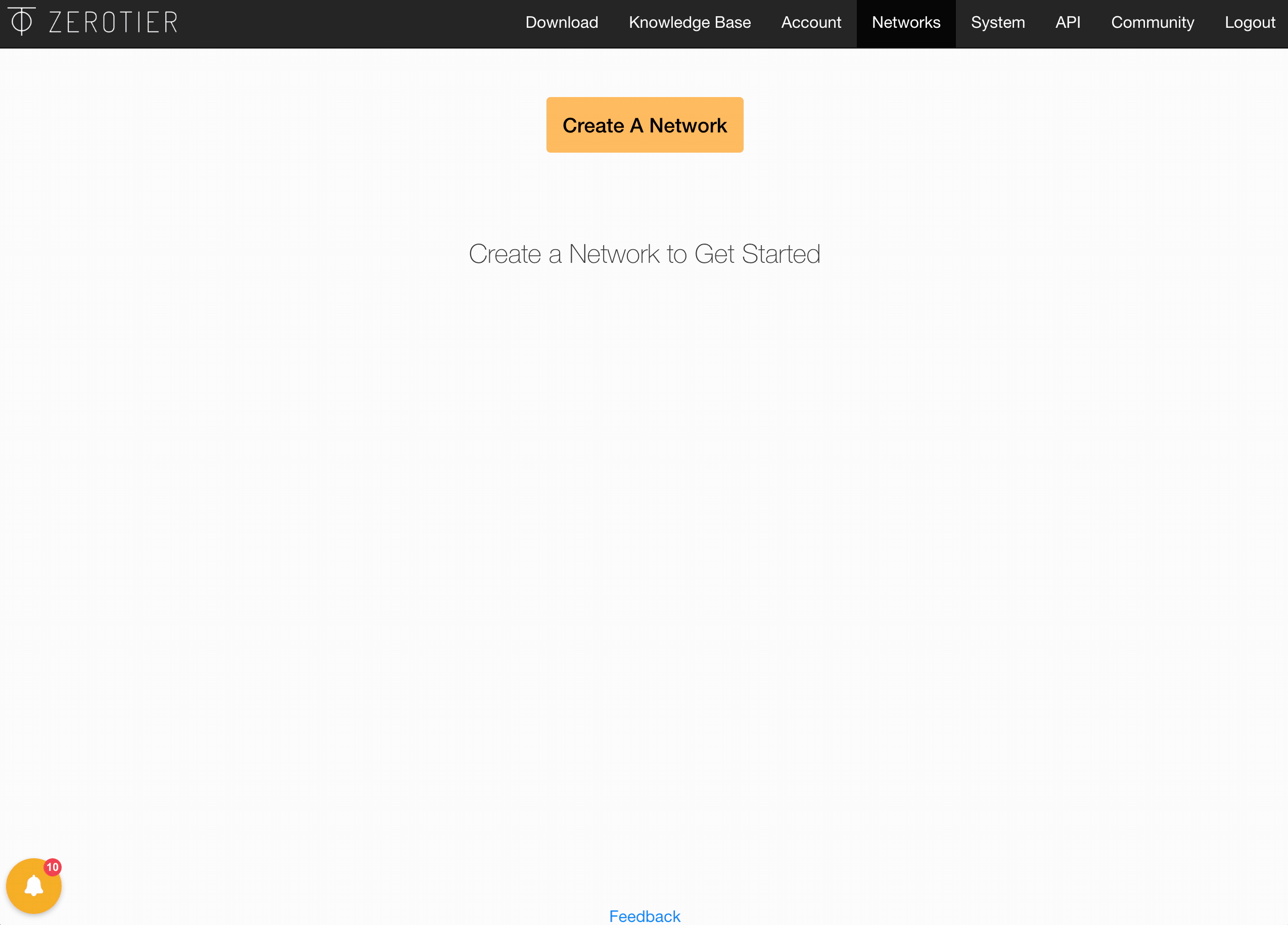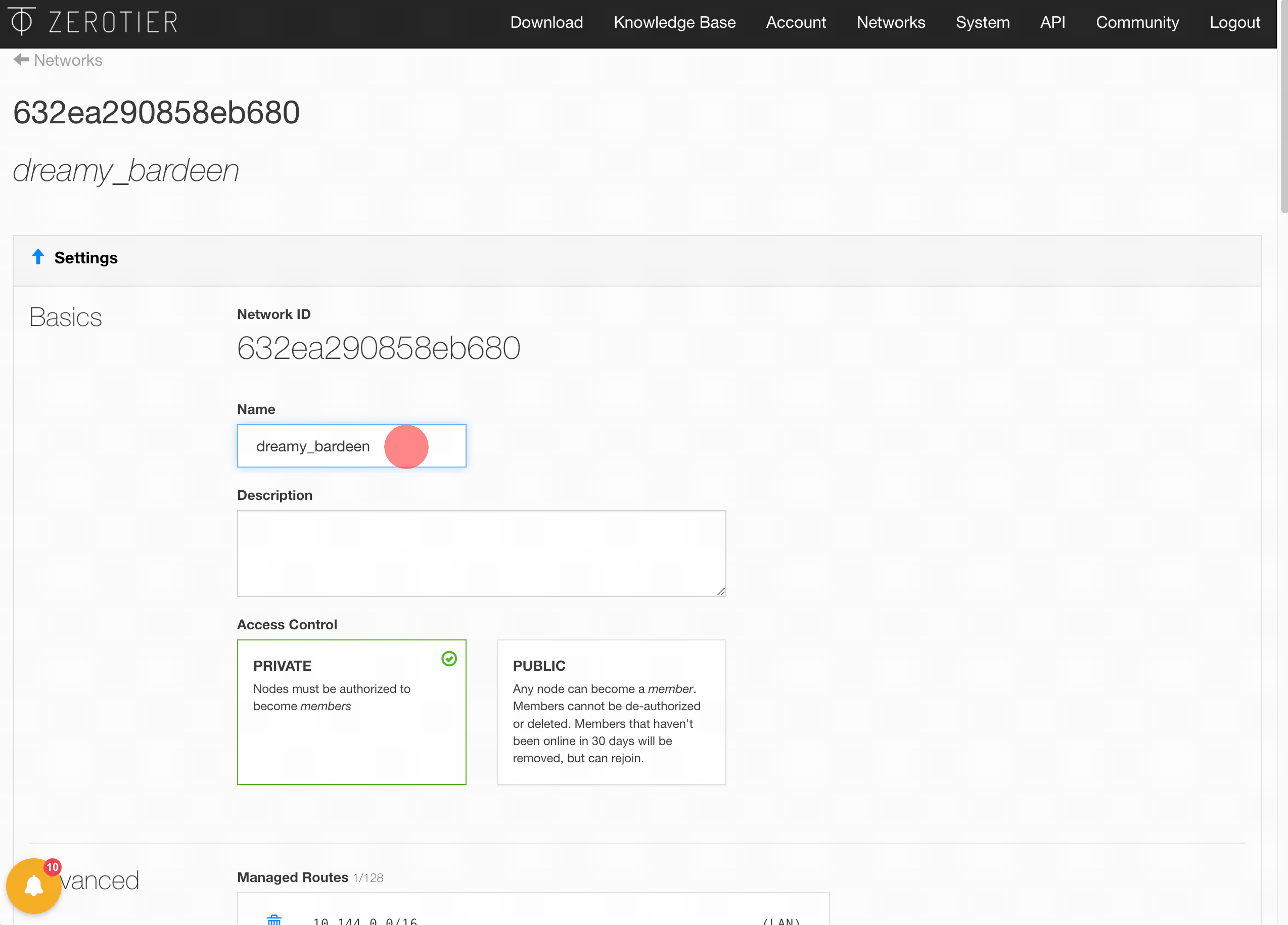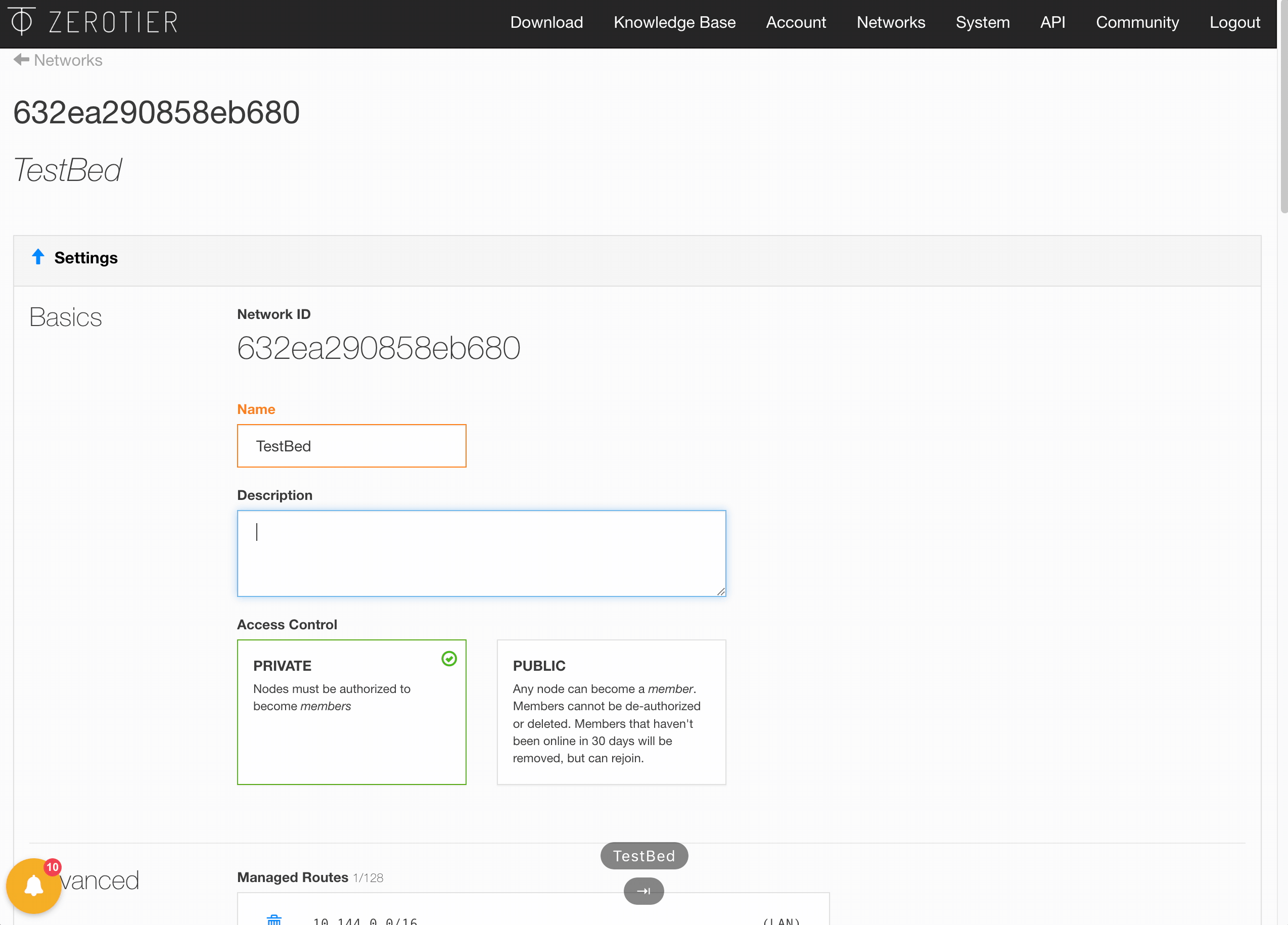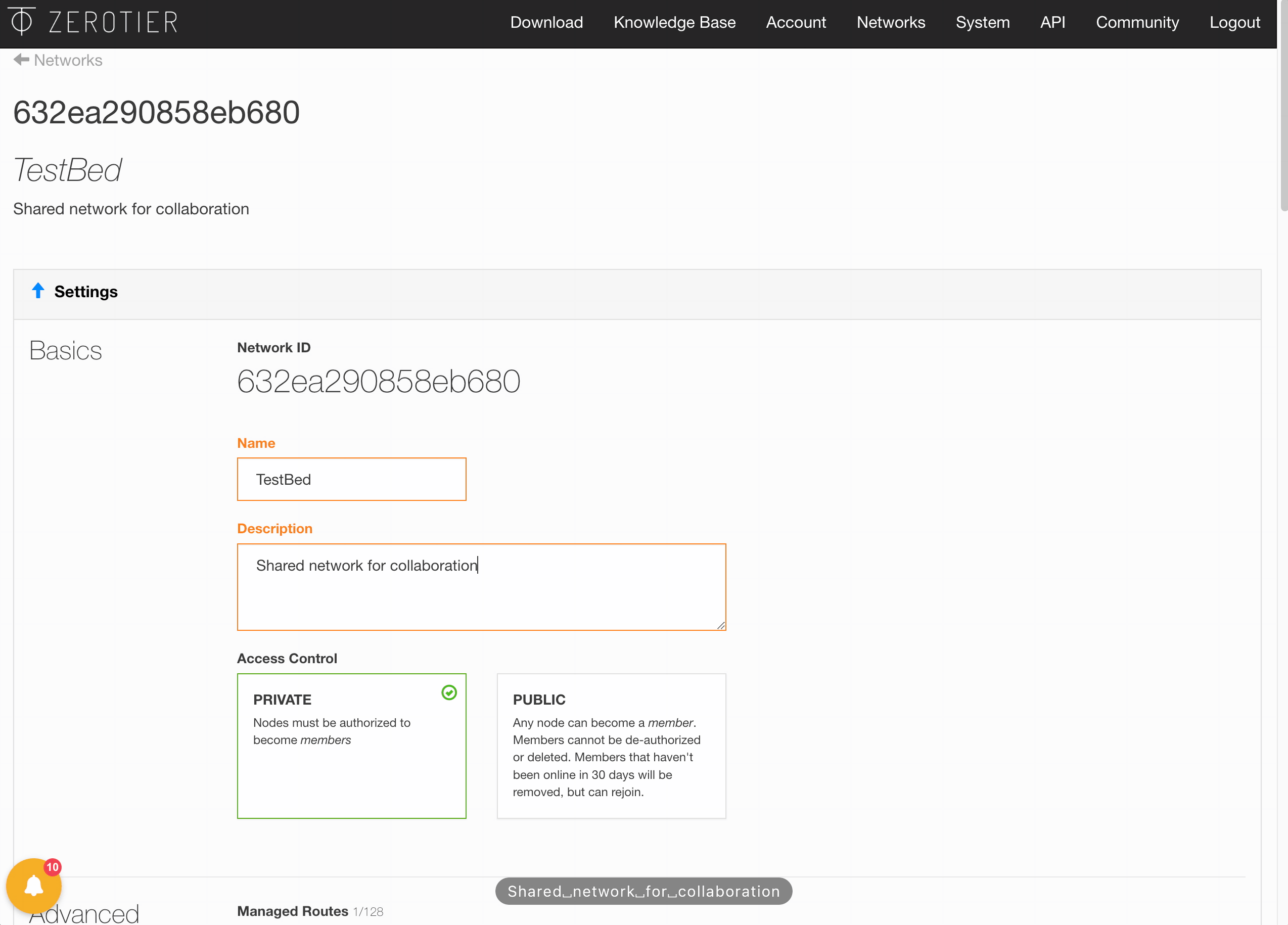
First, we need to sign-up for a ZeroTier Account. Each VL2 network is identified by a 64-bit (16 hex digit) ID. Once our email is confirmed, we can create a network, add a new friendly name + description, and retrieve the Network ID.
Installing ZeroTier Plugin#
Next, let’s install the ZeroTier plugin on the OPNsense instance in front of the lab.

Configuring OPNsense#
Now, we need to configure the ZeroTier service on OPNsense. First, we must enable the service, and then we can add the network using the Network ID generated when we created the network in the ZeroTier portal.
Authorizing New Members#
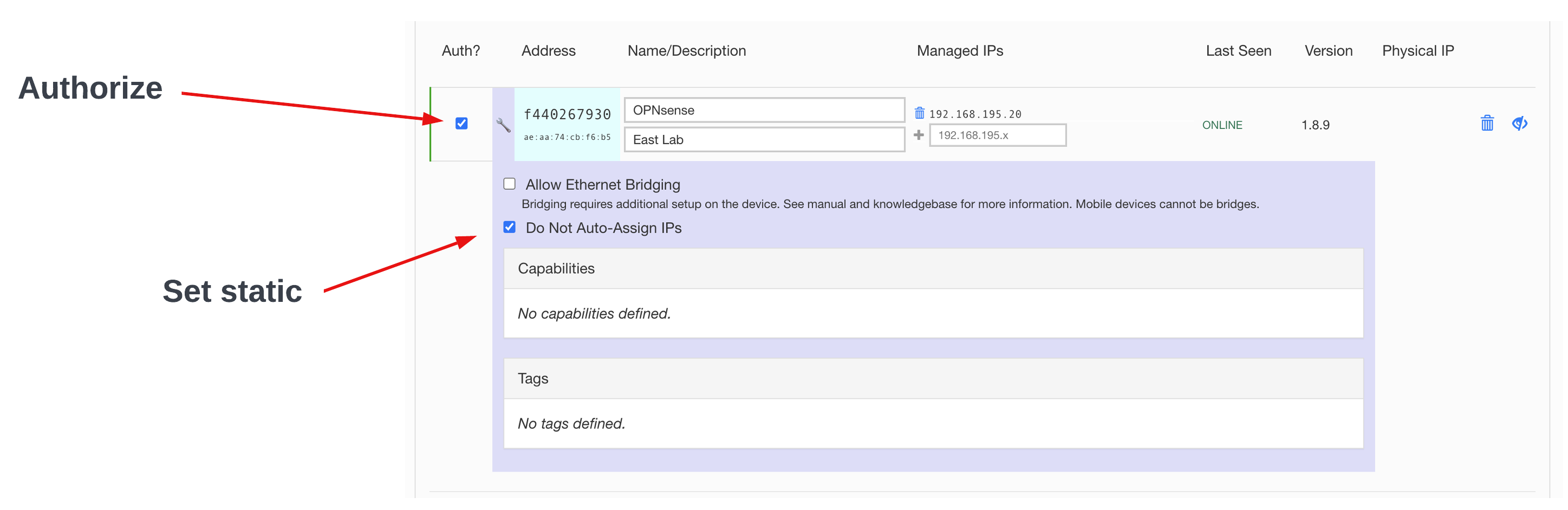
After we add the network in OPNsense, we can hop back to the ZeroTier portal and authorize it. Since I want to enable access for others to this lab environment, I’ll be setting up a managed route with the destination as the RFC1918 space of the lab with the OPNsense instance as the gateway. To prevent any future confusion, I configured Do Not Auto-Assign IPs when authorizing, and configured the managed IP statically.
Assigning the ZT Interface#
If you navigate to Interfaces > Assignments, you should see a new interface populated. We need to add this interface and assign a static IPv4 address using the managed IP we set in the ZeroTier portal.
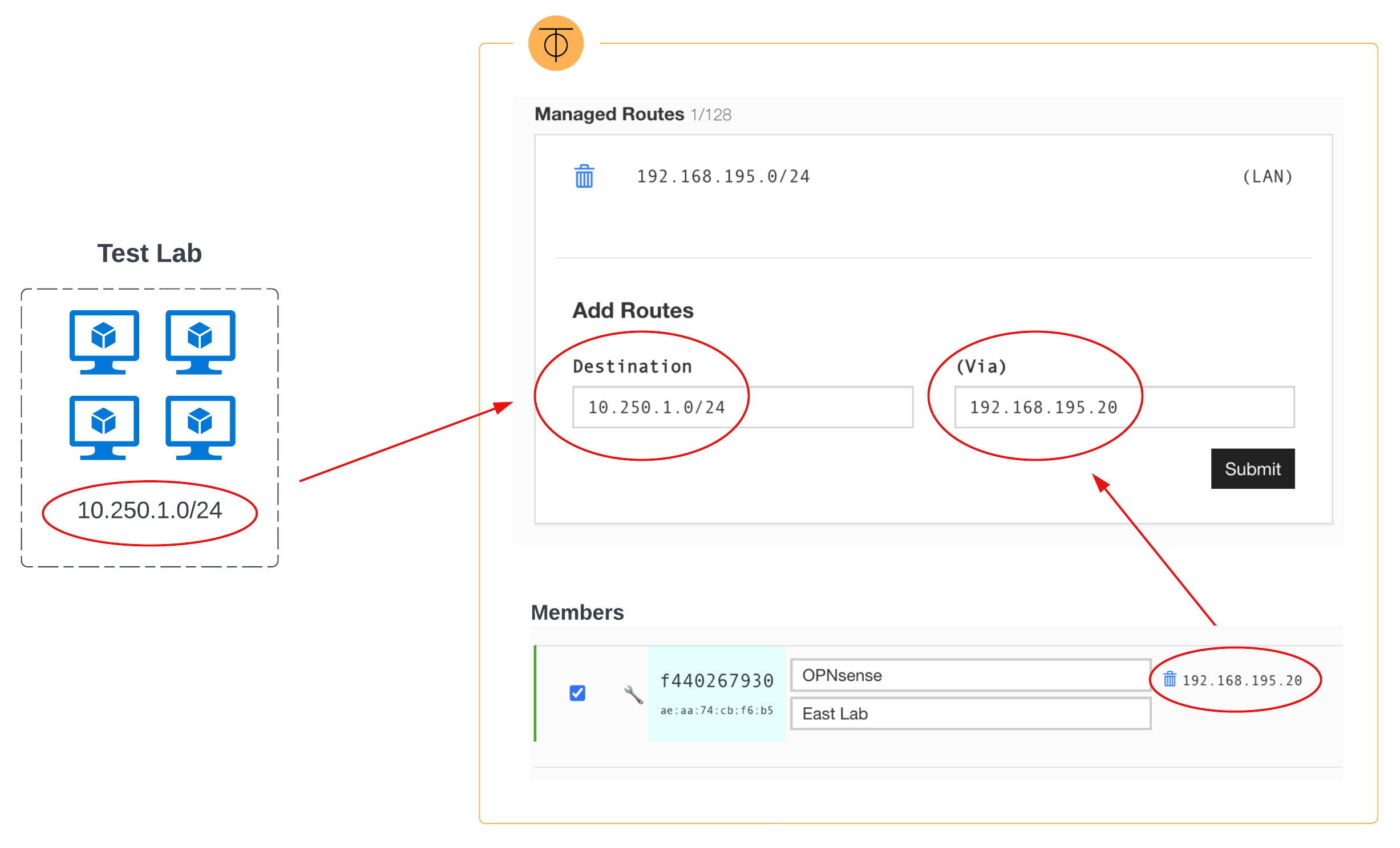
Adding a Managed Route#
To route traffic beyond the OPNsense instance, we need to add a managed route in ZeroTier. For the destination, we will use the RFC1918 space for the lab environment. For the gateway (Via), we will use the managed IP we set for OPNsense in the ZeroTier portal.
Allowing Traffic on OPNsense#
To allow communication from other ZeroTier members into our lab environment, we need to add a firewall rule on the ZeroTier interface in OPNsense. Of course, since this is a blog, I’m committing the cardinal sin of inserting an any-to-any rule. Avoid doing this as a general practice!
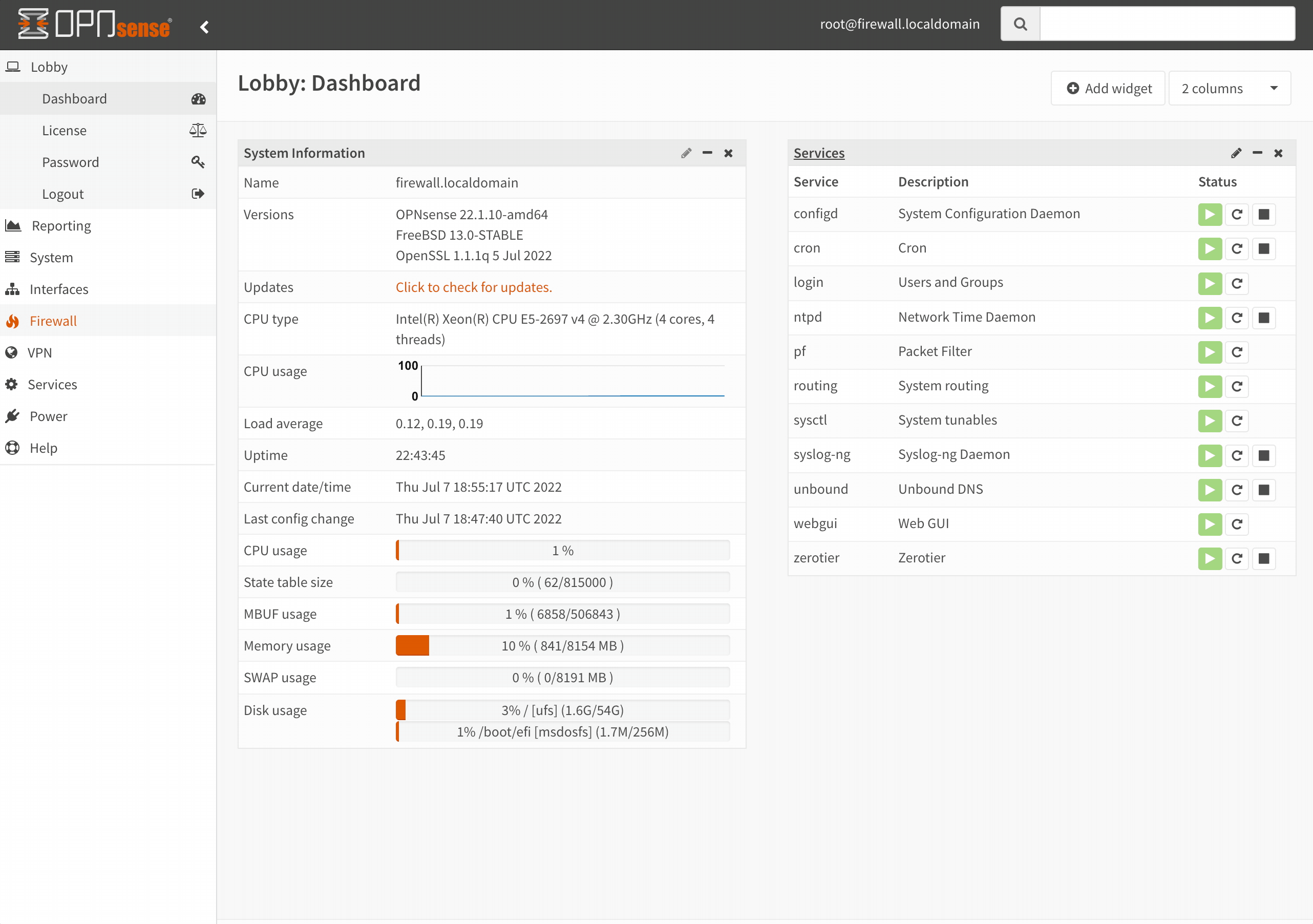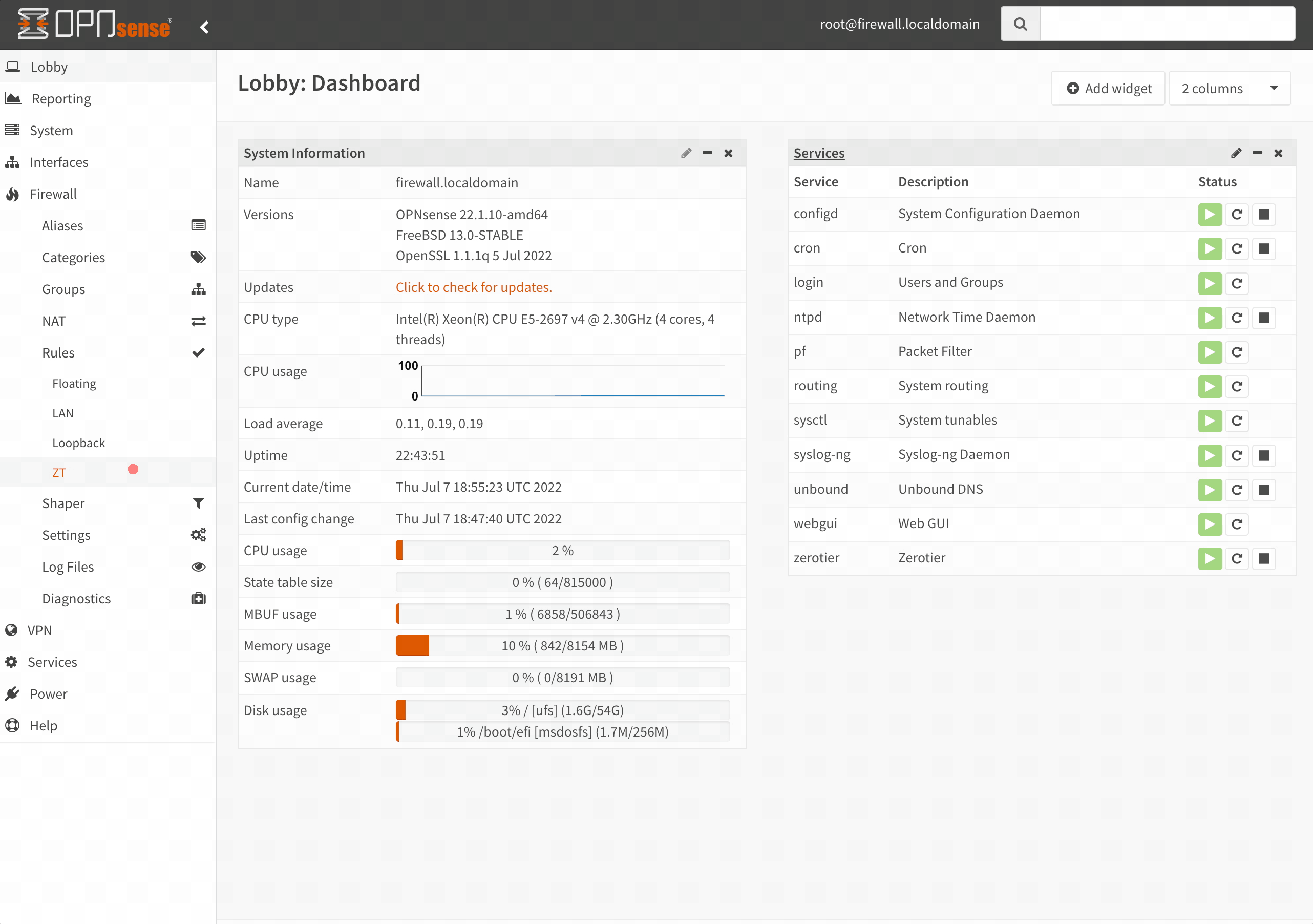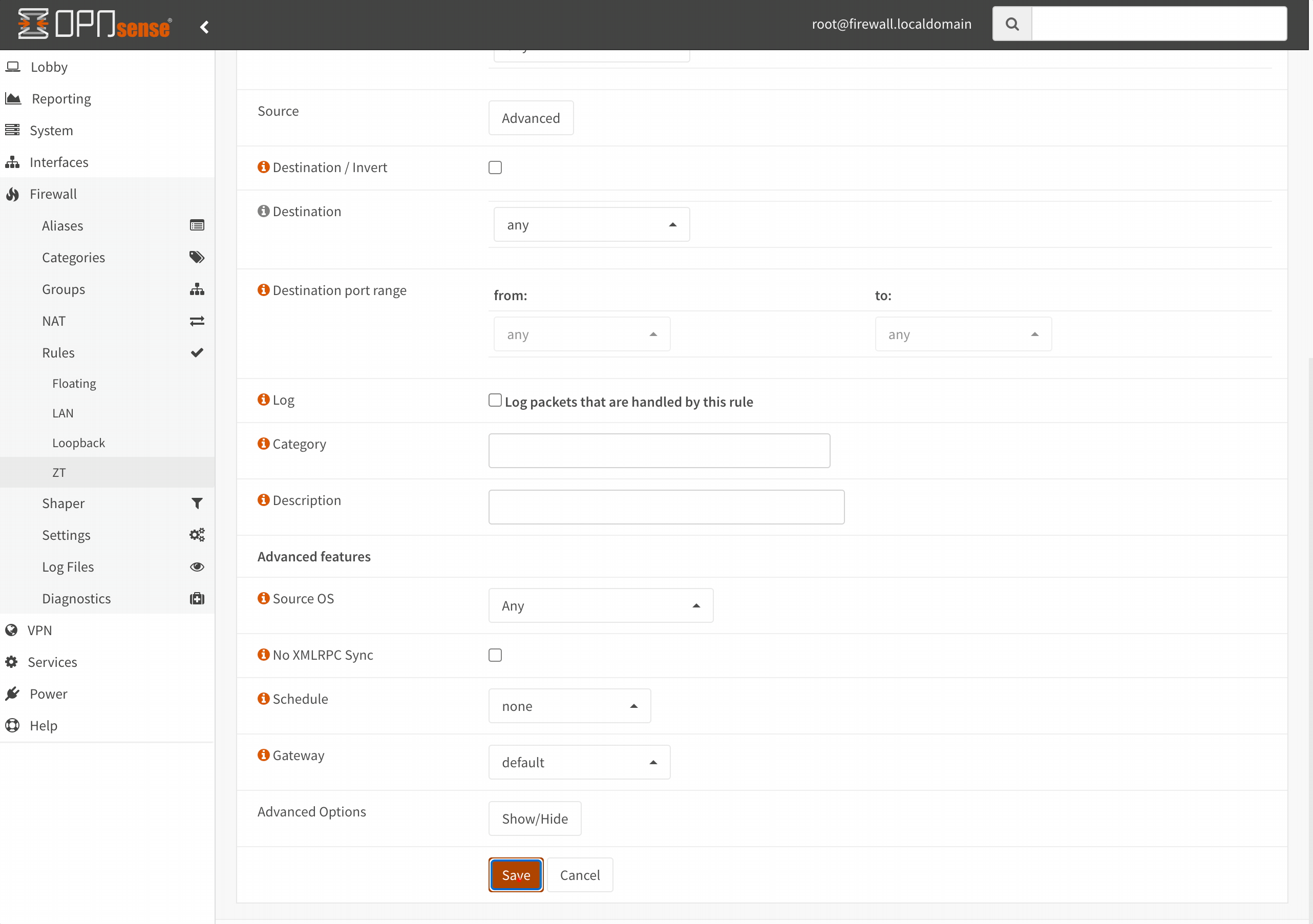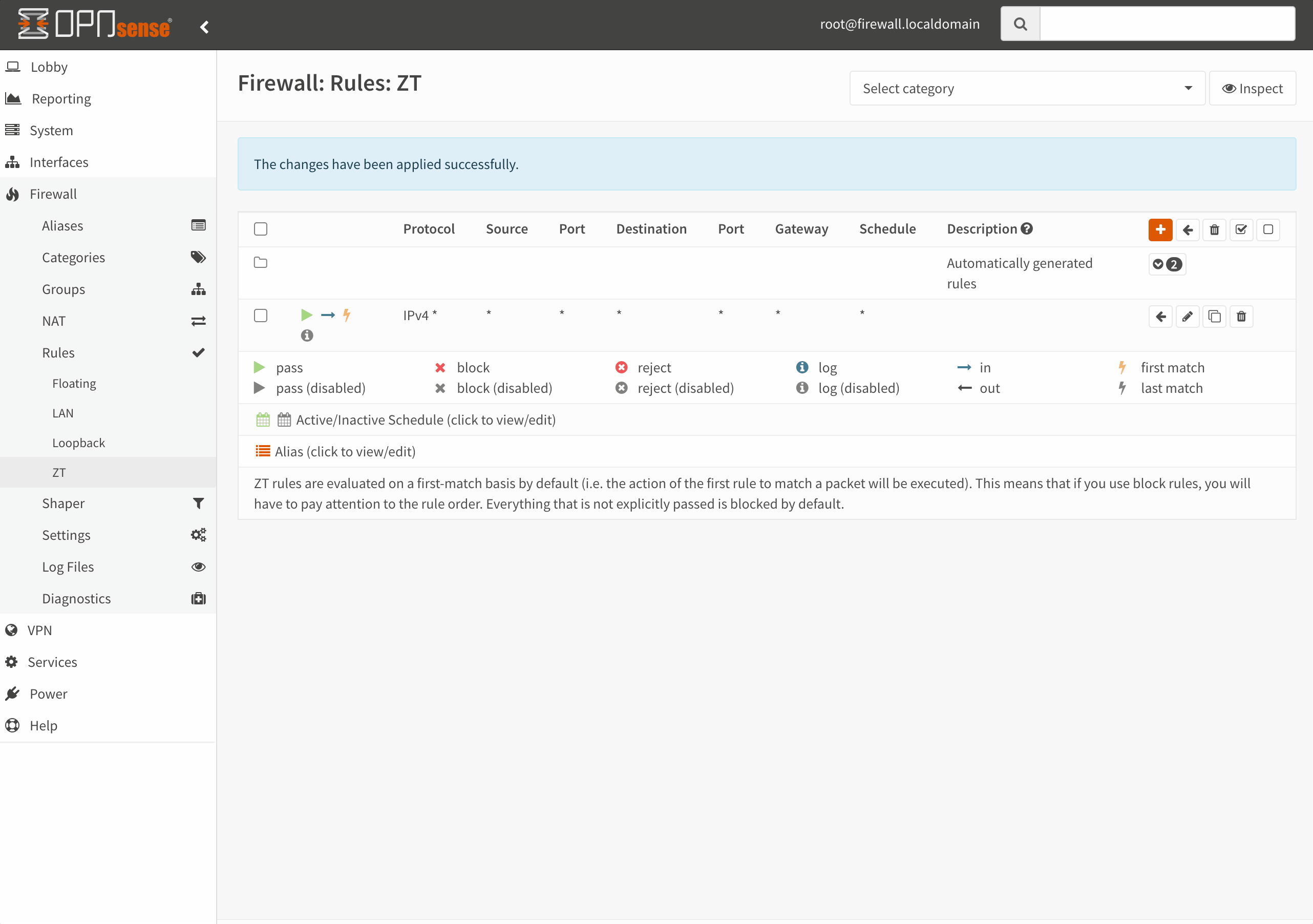
ZeroTier uses UDP hole punching, which essentially tricks the router into allowing access to a port on a device directly without establishing a TCP session. Since firewalls are stateful, they keep track of connections. Since UDP doesn’t establish a session, there is only a concept of inbound/outbound packets on the firewall. This means the firewall has to rely on limited data to let returning packets through (UDP 5-tuple data).
Connecting from Client Devices#
You can find the ZerTier One application on Google Play or the Apple Store. Once the app is downloaded, you can provide the network ID and click Join Network to connect. Downloads for other platforms can be found here.
ZeroTier SDK#
Want to enable a mobile app to join a network without requiring special permissions on the phone or adding a tun/tap port? The ZeroTier SDK takes the network hypervisor and couples it with an embedded TCP/IP stack which you can link into an application library. This essentially moves the network stack into the application itself.
Conclusion#
Mesh VPNs offer a thought-provoking alternative to traditional hub-and-spoke designs. It would be interesting to see what a large-scale deployment would look like in the typical risk-averse enterprise and how the migration path would play out. Tailscale seems to be the biggest competitor in this space and more or less does the same thing, just using different protocols. While ZeroTier’s protocol is proprietary, Tailscale uses Wireguard for its data plane. I look forward to seeing how remote work evolves over the next few years.